Just enough security & compliance permissions for Just In Time access
- Shahin Basheer

- Jan 24, 2023
- 3 min read

It is often the requirement of large organisations to grant security and compliance roles to non IT staff members of different sections. In this article we take a look at the challenges and its solution while granting the minimum security & compliance permissions for limited time access with proper control and auditing.
Grant the minimum permissions
Microsoft has provided many built-in 'Role Groups' such as Compliance Administrator, eDiscovery Manager, Security Administrator, etc., which can be used for the various job roles. These 'Role Groups' and associated role permissions can be verified in the permissions tab in Microsoft Purview compliance portal. However they may not be adequate for various use cases.
For example, 'Content Explorer' is one of the most debated features in the compliance portal which allows to list, view and verify actual contents in Microsoft 365 classified against Sensitive info types, Trainable Classifiers, Sensitivity labels and Retention labels. Often the organizations would have 'Data Protection Officers' who are authorised to use Content Explorer to analyse the contents. Its common for admins to grant the 'Compliance Administrator', 'Content Explorer List Viewer' and 'Content Explorer Content Viewer' 'Role Groups' to the DPO which allow them to use the Content Explorer. Eventually the DPO has more permissions in the compliance portal than required.
Grant the access for limited time with proper control & auditing
Most organisations have Azure privileged identity management configured for Just In Time role access. Any Azure AD roles can be configured for JIT assignments. Multiple Azure AD roles can be allowed at the same time for JIT access through the Privileged access groups feature (Preview as of this writing). However the 'Role Groups' in Security & Compliance portals are not available for assignment in the Azure privileged identity management.
Requirement | Solution | Challenge |
Grant the minimum permissions in Security & Compliance portals | Use the Role Based Access Control Groups from Security & Compliance Centre | Built-in 'Role Groups' does not meet the minimum permission requirements. |
Grant the access for limited time with proper control & auditing | Use Azure privileged identity management | Roles in Security and Compliance are not available as roles in Azure PIM |
Solution
Following are the step by step configuration to address the challenges
Create a security group with the 'Azure AD Role Assign' setting in Azure AD.
Enable the privileged access for the group.
Create a custom 'Role Group' with the minimum role permissions through Security & Compliance PowerShell. (Built-in 'Role Groups' are group of predefined role permissions).
Add the Azure AD security group as Member of the custom 'Role Group' through Security & Compliance PowerShell.
Add the required users to the eligible assignments in the group in Azure AD privileged identity management.
1. Create a security group with the 'Azure AD Role Assign' setting in Azure AD Groups.
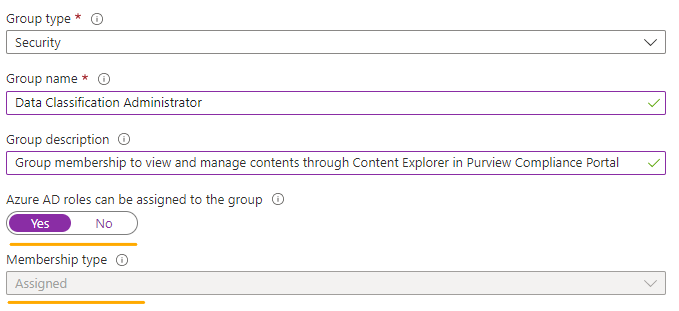
The Azure AD role assignability is an immutable setting. Ensure proper testing is done in test environment before configuring it in production.
2. Enable the privileged access for the group from the group properties tab created in previous step.
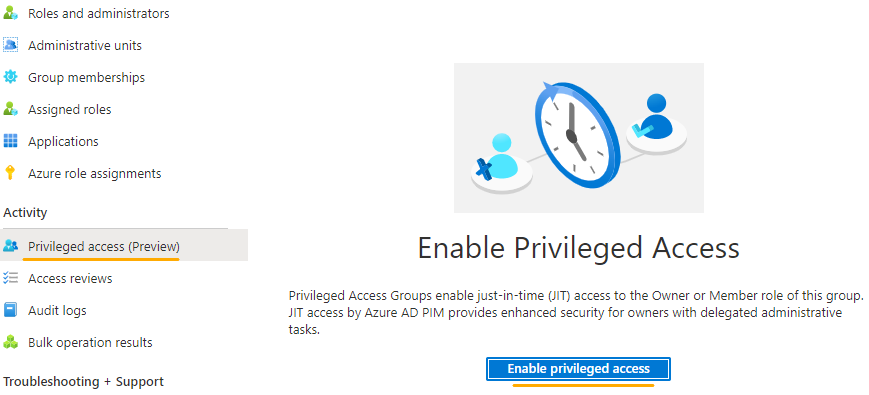
3. Create a custom 'Role Group' with the minimum permissions through Security & Compliance PowerShell
Connect-IPPSSession
New-RoleGroup -Name 'Content Administrator' -DisplayName 'Content Administrator' -Description 'Role Group for Content Explorer and Sensitive Info Type Management' -Roles 'Data Classification List Viewer','Data Classification Content Viewer','Data Classification Feedback Provider', 'Data Classification Feedback Reviewer', 'Data Investigation Management', 'View-Only DLP Compliance Management'
This step creates a custom 'Role Group' with minimum permissions for allowing Content Explorer and other data classification tool management in Purview compliance portal. This step can be done from the compliance portal, permissions tab. Other custom 'Role Group's can be created by adding only the required role permissions.
4. Add the Azure AD security group as Member of the custom 'Role Group' through Security & Compliance PowerShell
Add-RoleGroupMember -Identity 'Content Administrator' -Member 'Data Classification Administrator'
This step adds the Azure AD security group as a member of the 'Role Group'. Please wait few minutes before the security group can be added as member to the 'Role Group'. This step can only be done from the PowerShell, since compliance portal does not allow to add security groups as members. Once the group is added as a member, membership can be verified from the compliance portal permissions tab.

5. Add the required users to the eligible assignments in the group in Azure AD privileged identity management

Navigate to Privileged Identity Management in Azure portal.
Click on the Privilege access groups (preview) and select the Azure AD group created in previous step.
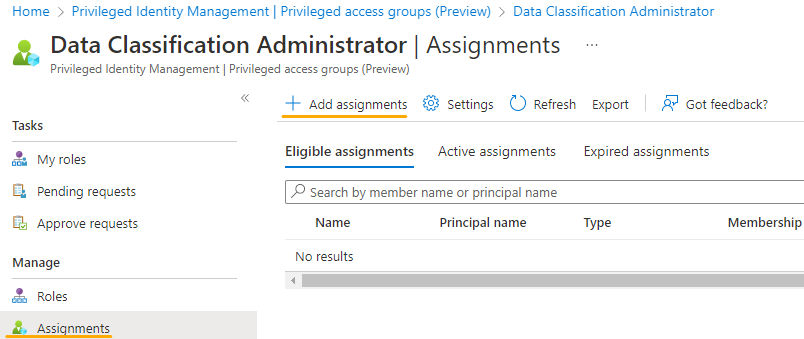
Click on the 'Assignments' options of the security group.
Click on 'Add assignments' and add the required users to the 'Eligible' assignment.
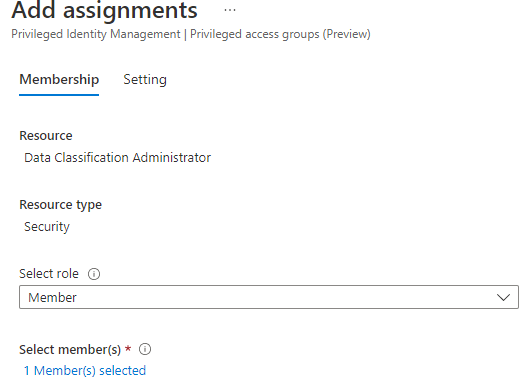
6. The users can now login to Azure Privileged Identity Management and activate the group membership

It might take some time for the roles to be reflected once the privilege access group is activated based on the roles added.
Many organisations fail to effectively identify and realise the value of Microsoft Purview features despite having full E5 licenses for years. Infotechtion experts can help you configure all Microsoft Purview Compliance solutions based on our extensive experience with Microsoft Cloud. Feel free to contact us or request demo of purview solutions.



Comments